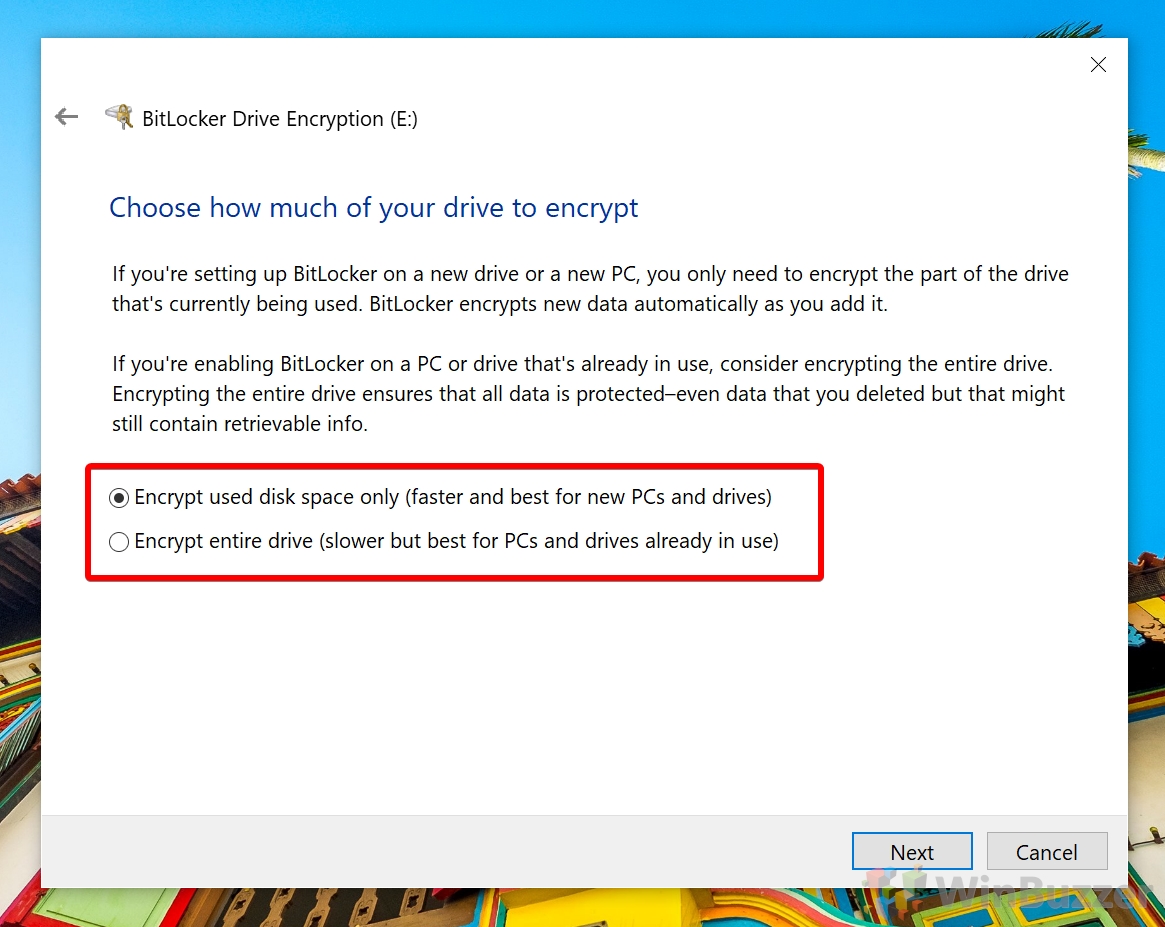
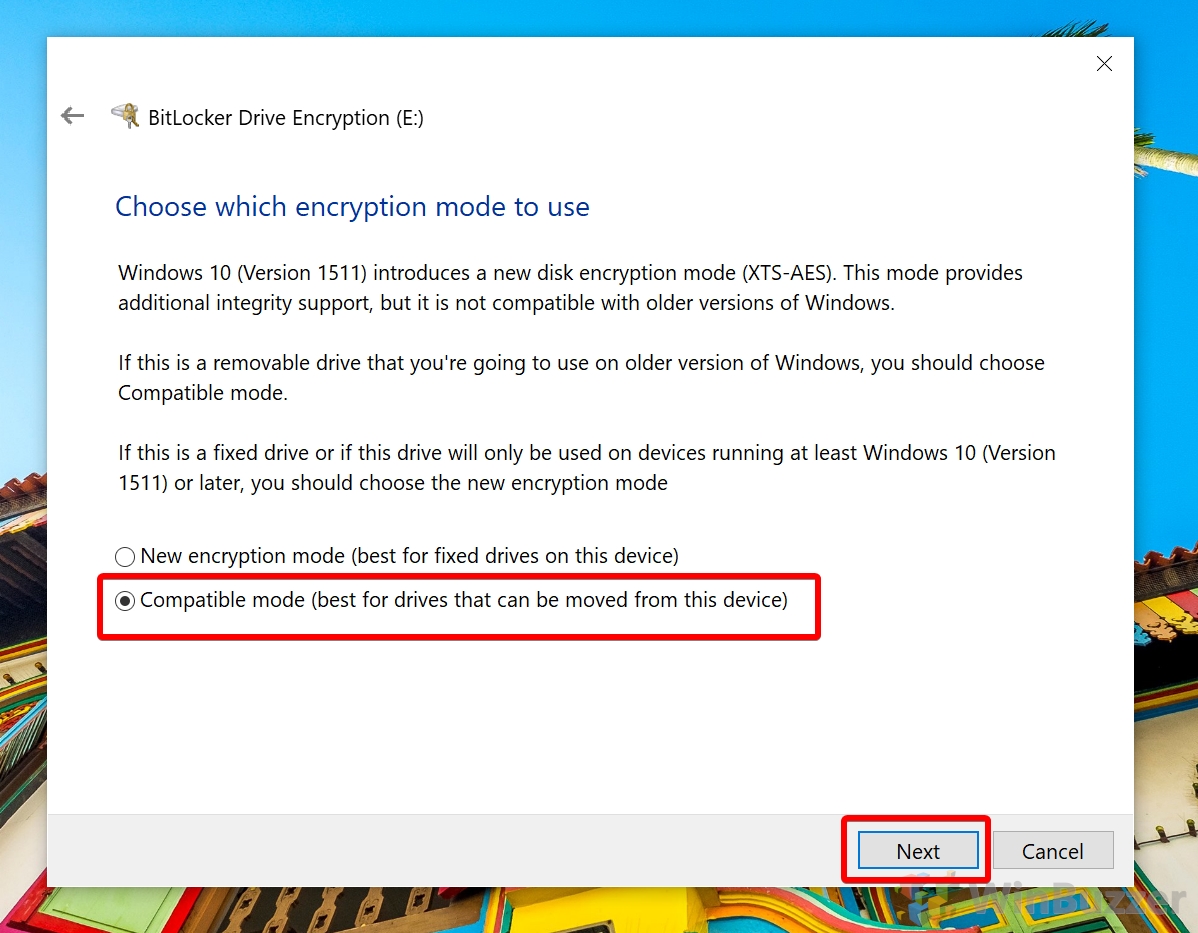
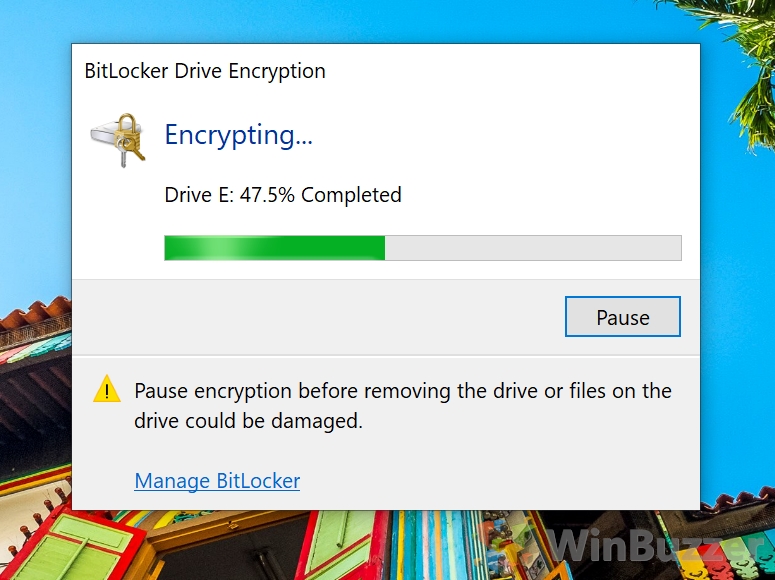
1 How to Check for Trusted Platform Module2 How to Allow BitLocker for Windows 10 Without a Compatible TPM via Group Policy Editor3 How to Encrypt System Drive with BitLocker4 Check Encryption Status and Change Bitlocker Settings for System Drive5 How to Use Bitlocker for non-system disks / BitLocker To Go to Encrypt a USB Drive, External Hard Drive or Secondary Drive6 How to Check Encryption Status and Change BitLocker Settings for USB Drives / Secondary disks
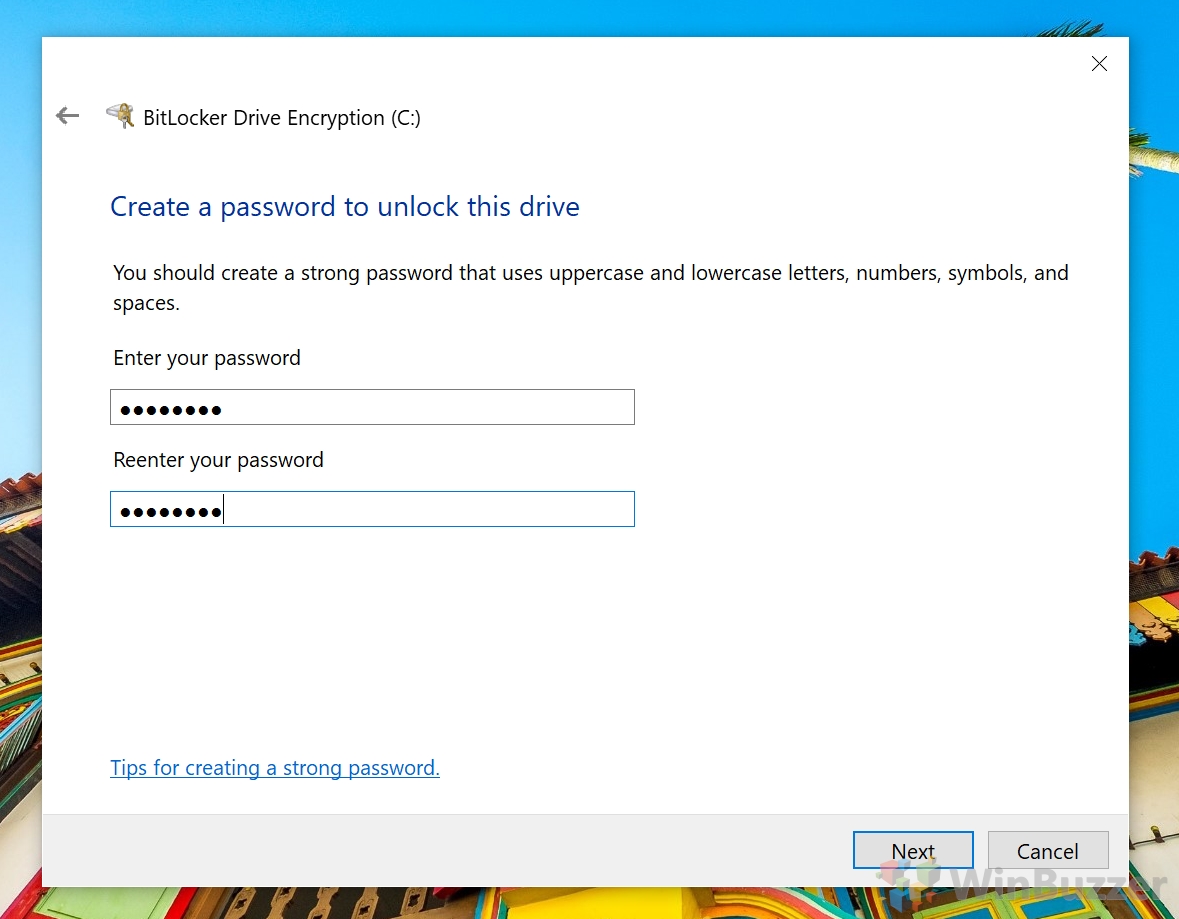
This means that a person doesn’t need to log in to your PC to steal your information. If your laptop gets stolen, they can simply use a bootable USB drive to take the data directly from your disks and view it on another PC. In some cases, drives that don’t use Windows BitLocker contain personal photos and information that can be used for identity theft. Depending on your browser configuration, they can also store passwords for your online accounts. Thankfully, BitLocker setup in Windows 10 isn’t difficult and you don’t even need to download BitLocker separately. Despite this, Microsoft doesn’t prompt you to create a BitLocker encrypted drive during setup or even explain what BitLocker does. We’re going to explain the benefit and show you how to password protect enable Bitlocker for your system drive with or without TPM. We’ll also be covering the use of BitLocker To Go to password protect an external drive in Windows 10, encrypt a USB drive, or encrypt a non-system partition on the main drive. What is BitLocker? BitLocker is a proprietary encryption program for Windows 10 that prevents unauthorized access to your drives and can protect against malware. When you perform BitLocker encryption on a drive, it’s transformed into random numbers and letters until you enter your BitLocker password or a USB key, which decrypts the drive. BitLocker in Windows 10 has three ways of usage
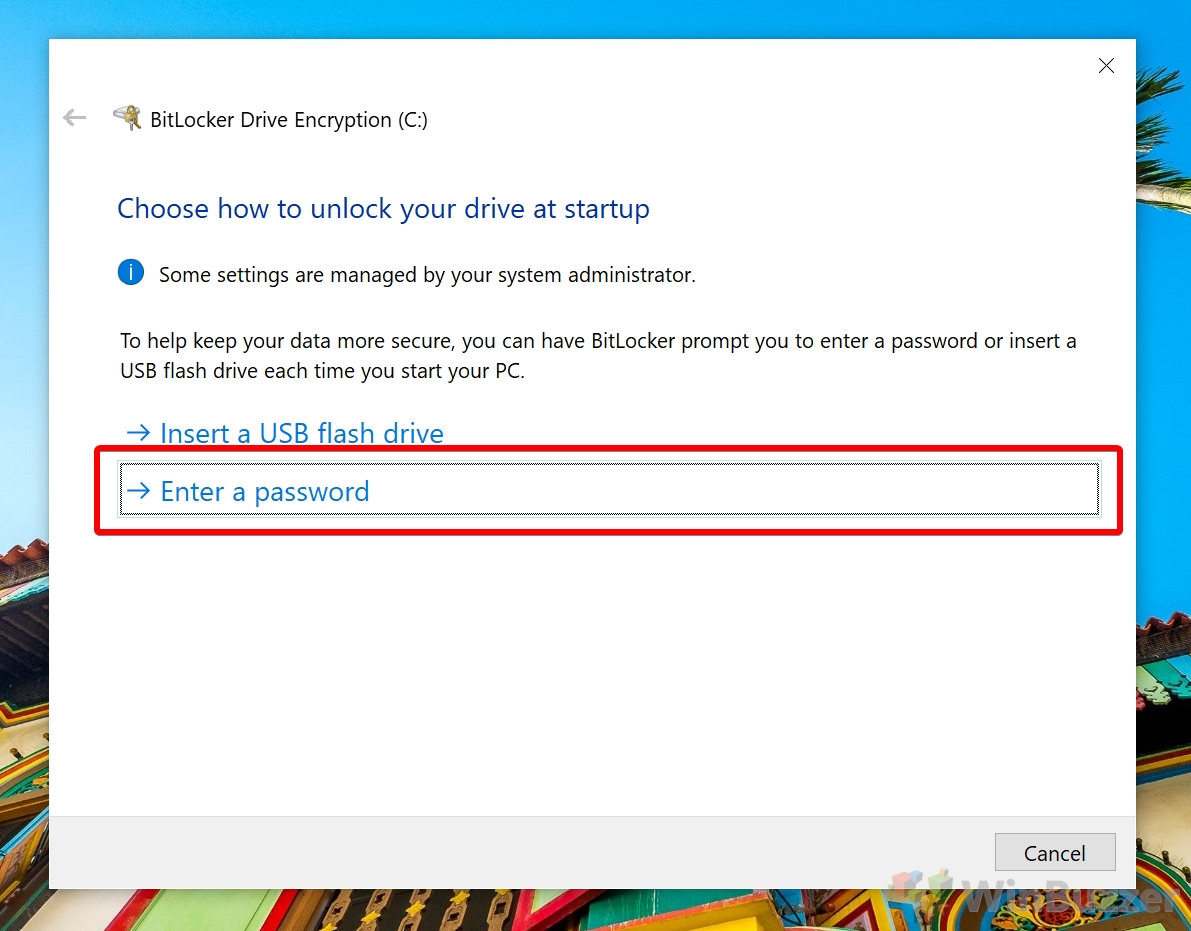
BitLocker for system drives makes use of the TPM chip or an optional unlock-screen to ensure integrity during boot and protect against malware that attacks the boot sector. BitLocker for non-system disks for any drive or partition other than the system partition. It doesn’t use TPM and doesn’t require an unlock at boot. BitLocker to go – a variant of BitLocker for non-system disks that is optimized for external drives connected via USB or other methods.
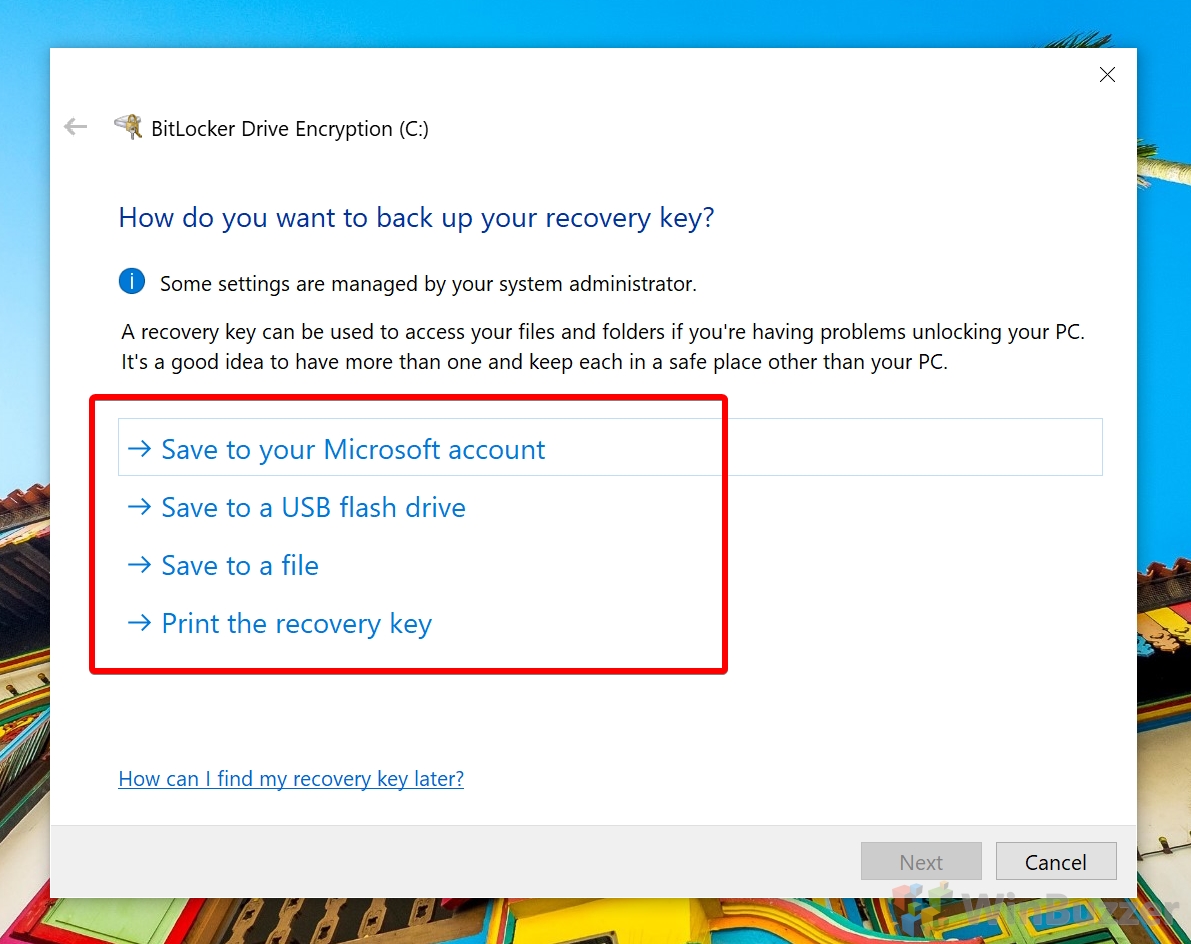
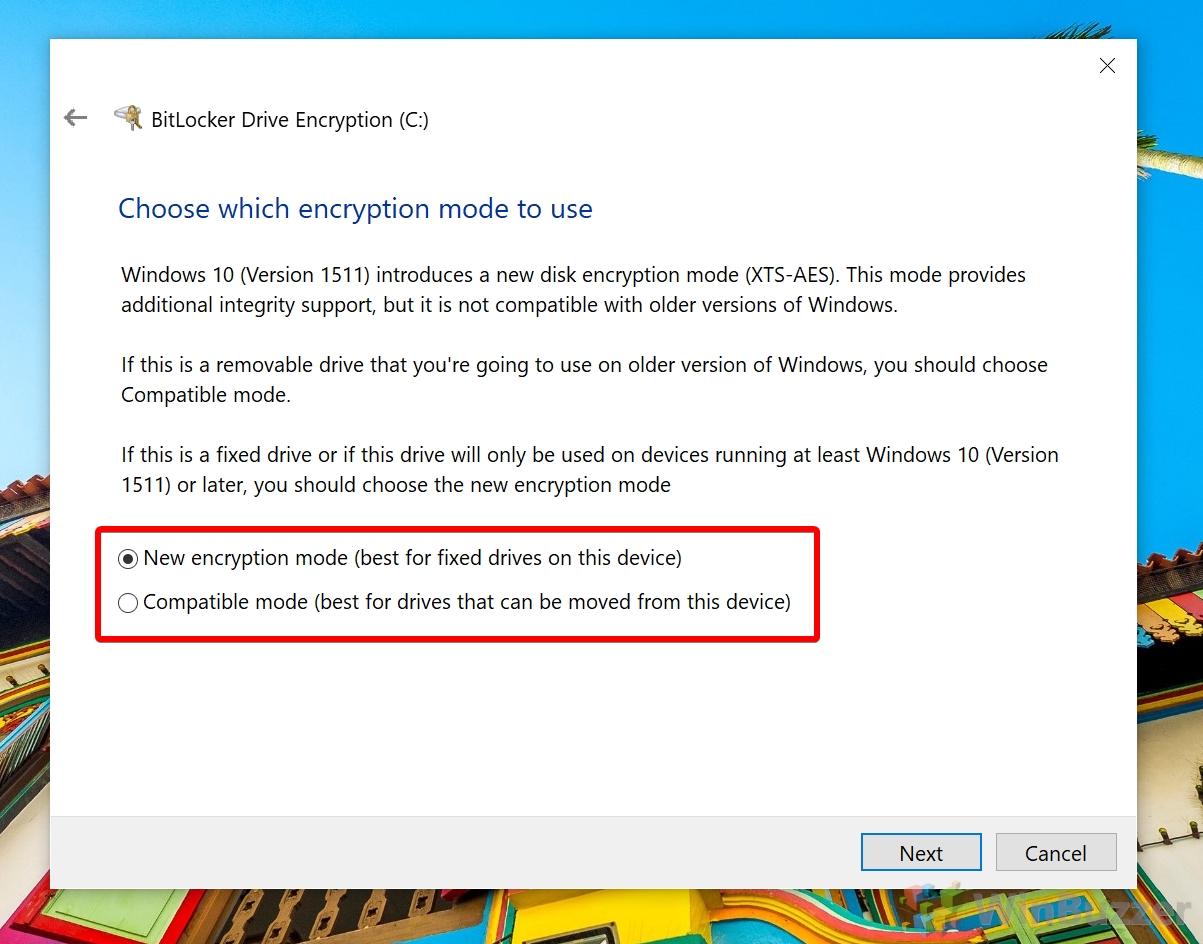
Though there have been a few successful attempts to bypass BitLocker, Microsoft has generally been quick to respond to them and has denied intelligence services a backdoor. As of Windows 10 1511, it comes with an XTS-AES encryption algorithm, further increasing security over Windows 8.1. As a result, it’s pretty much a no-brainer to use BitLocker drive encryption. It’s only going to increase security, and the downsides are small: the inability to access that data from non-Microsoft OS’, a very minor hit to disk performance, and loss of access to the data if you don’t back up your recovery key properly. Let’s get started with the tutorial:
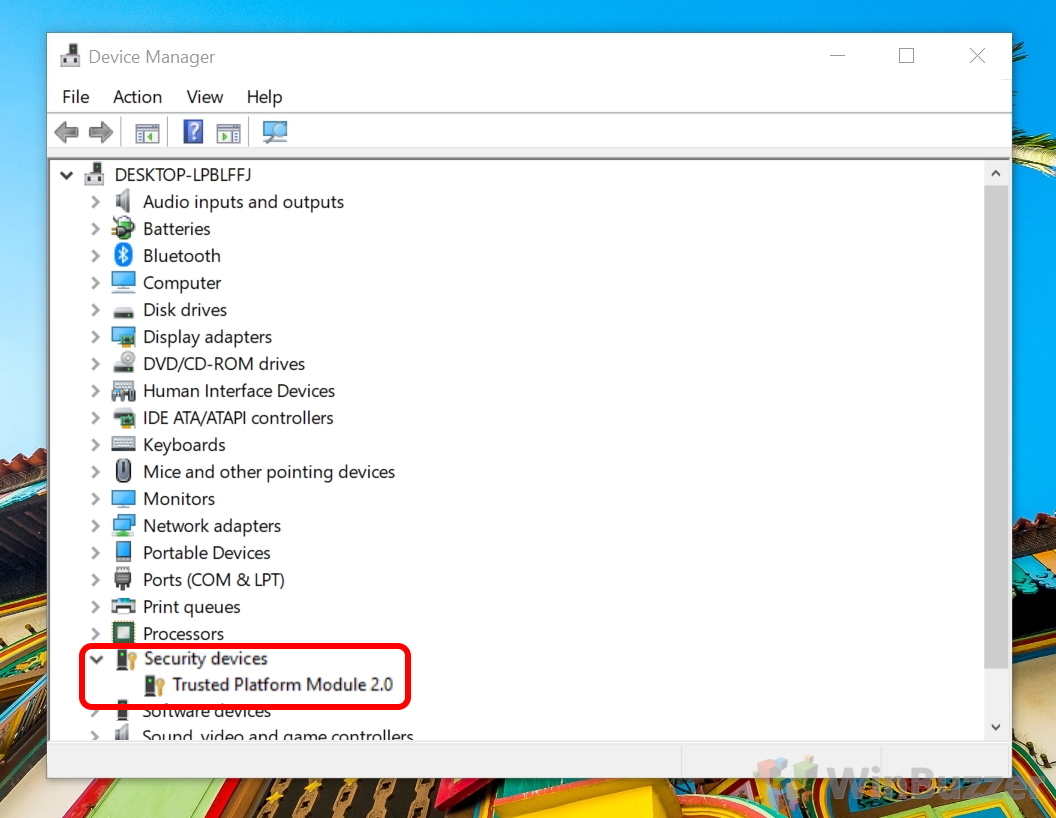
How to Check for Trusted Platform Module
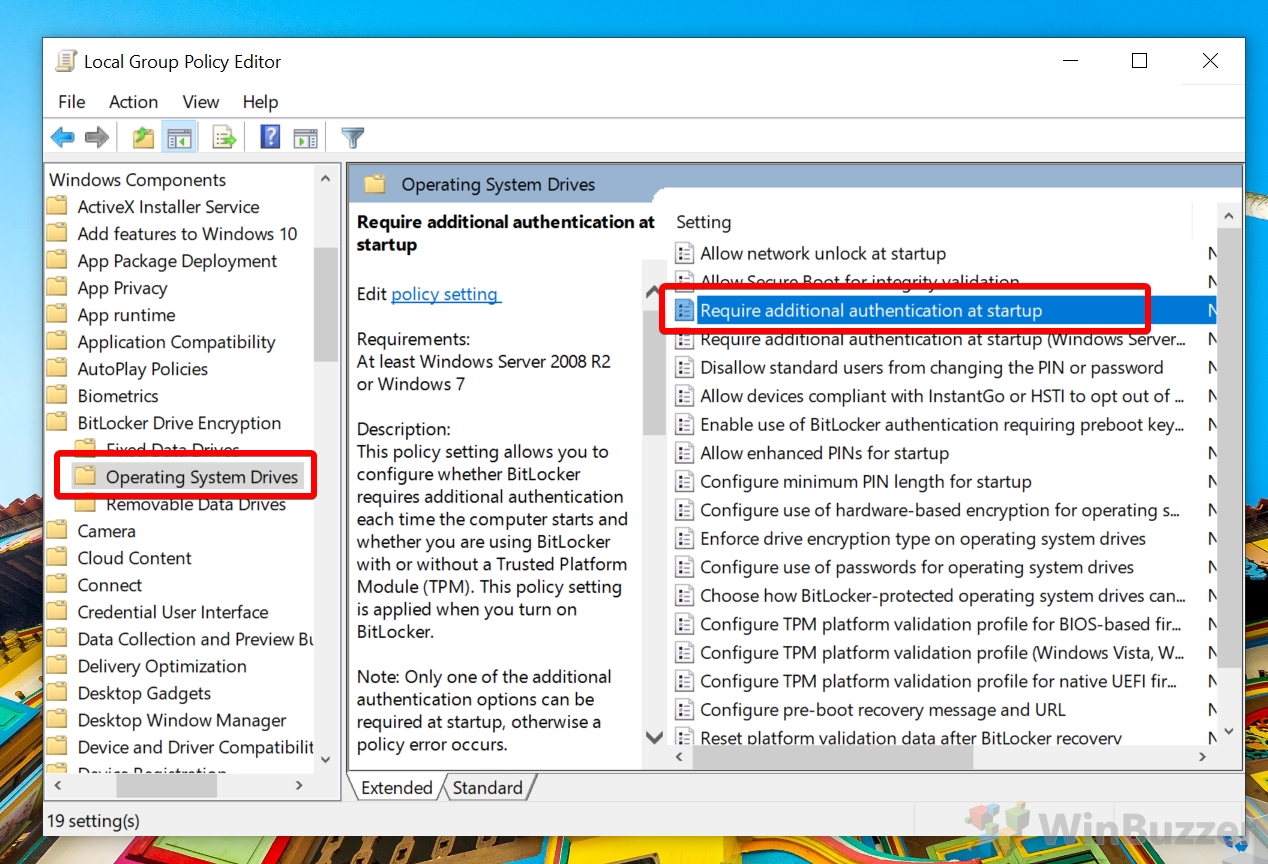
How to Allow BitLocker for Windows 10 Without a Compatible TPM via Group Policy Editor
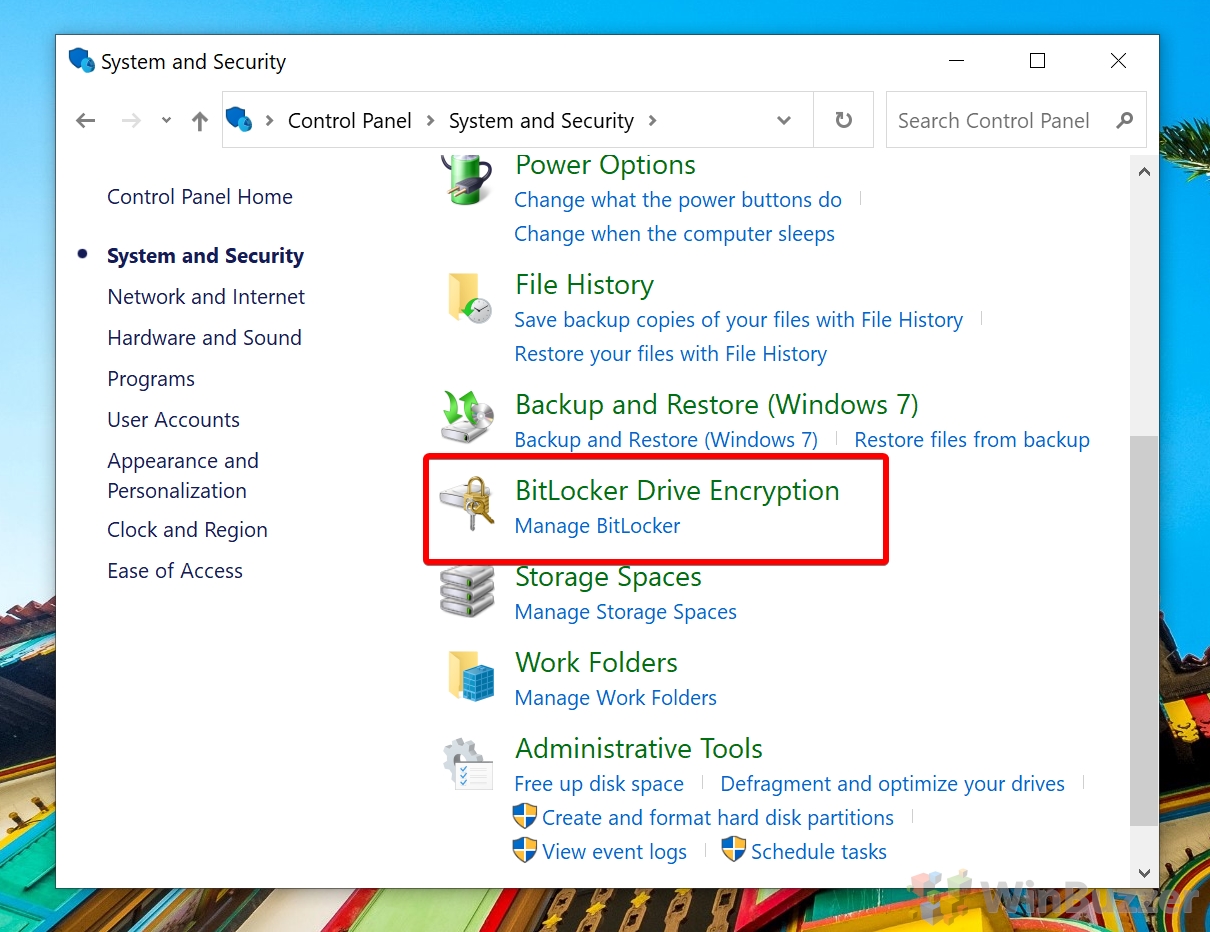
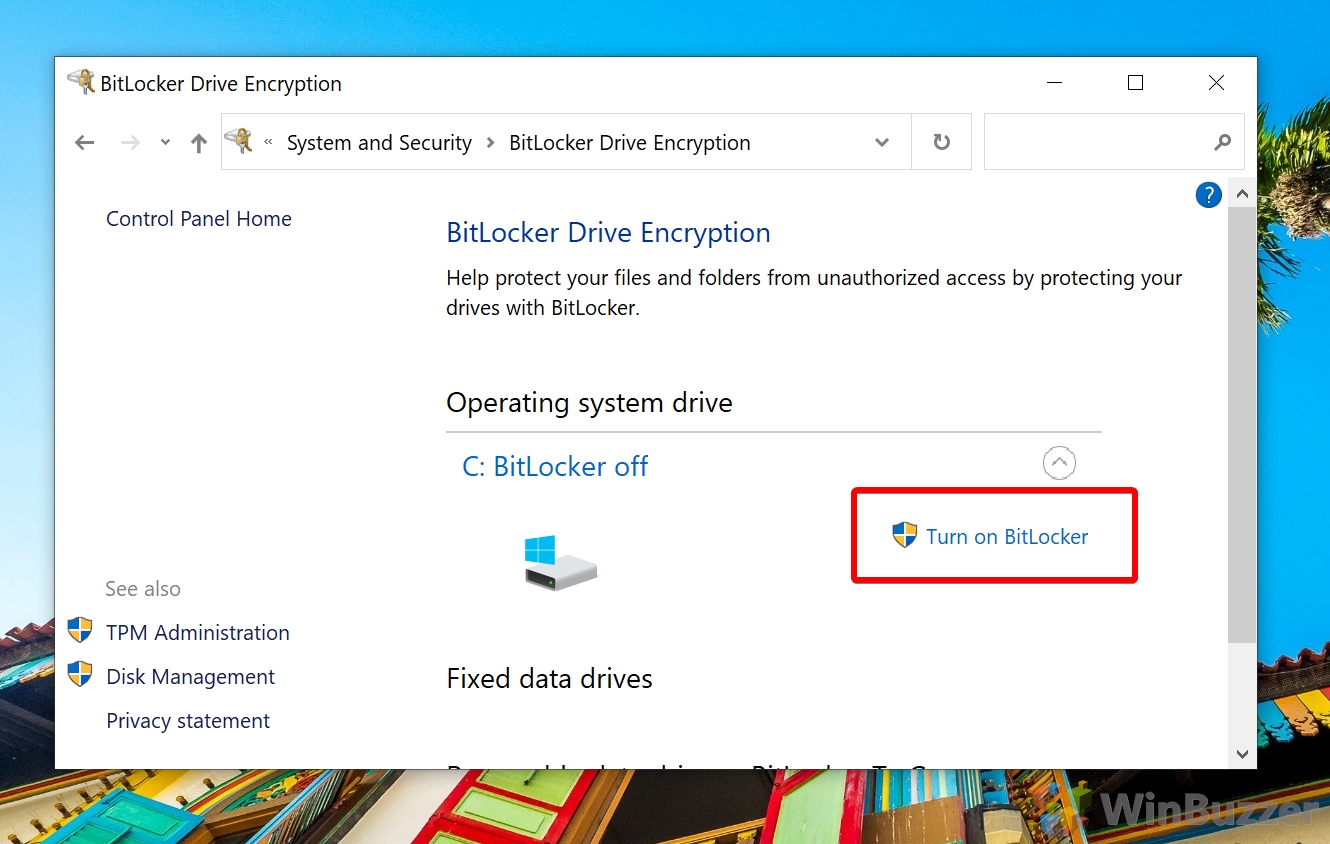
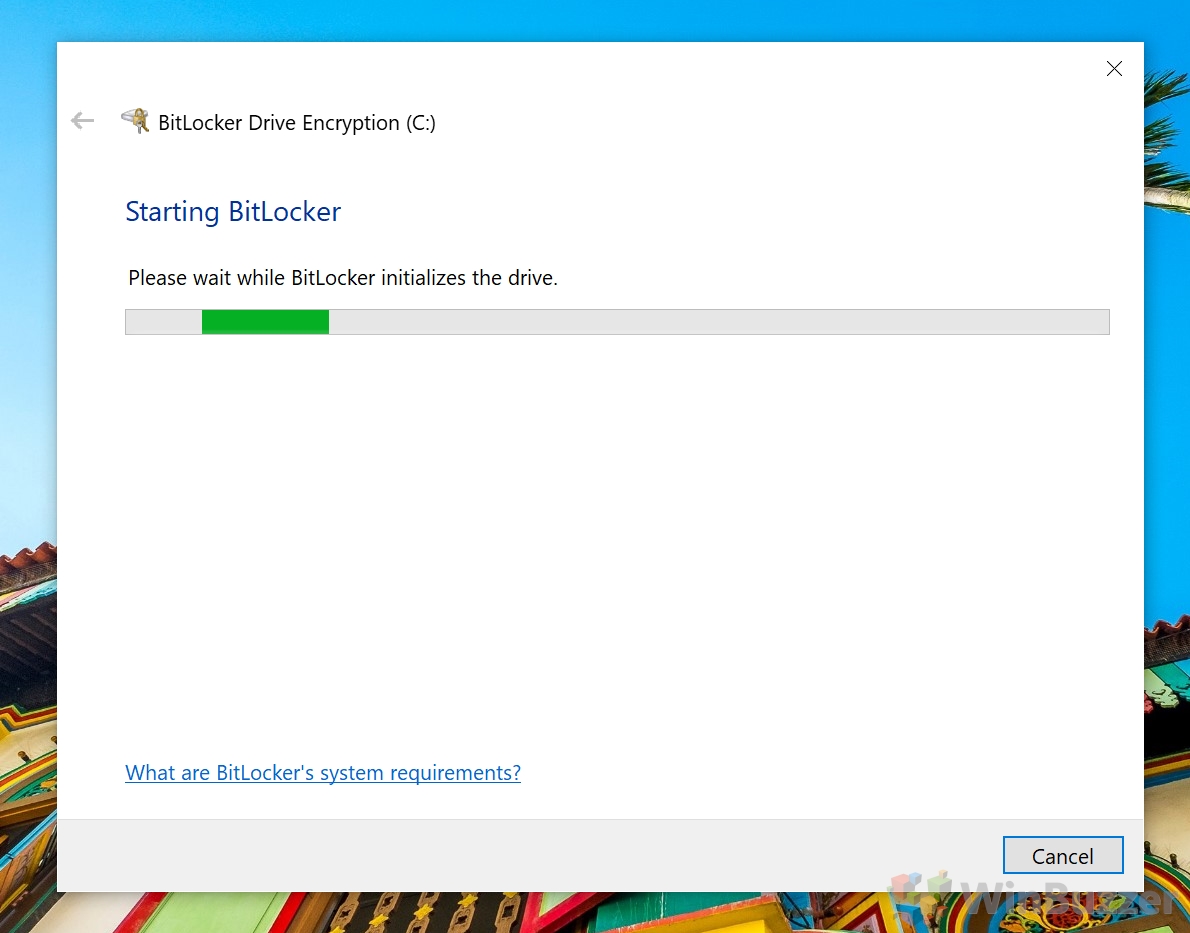
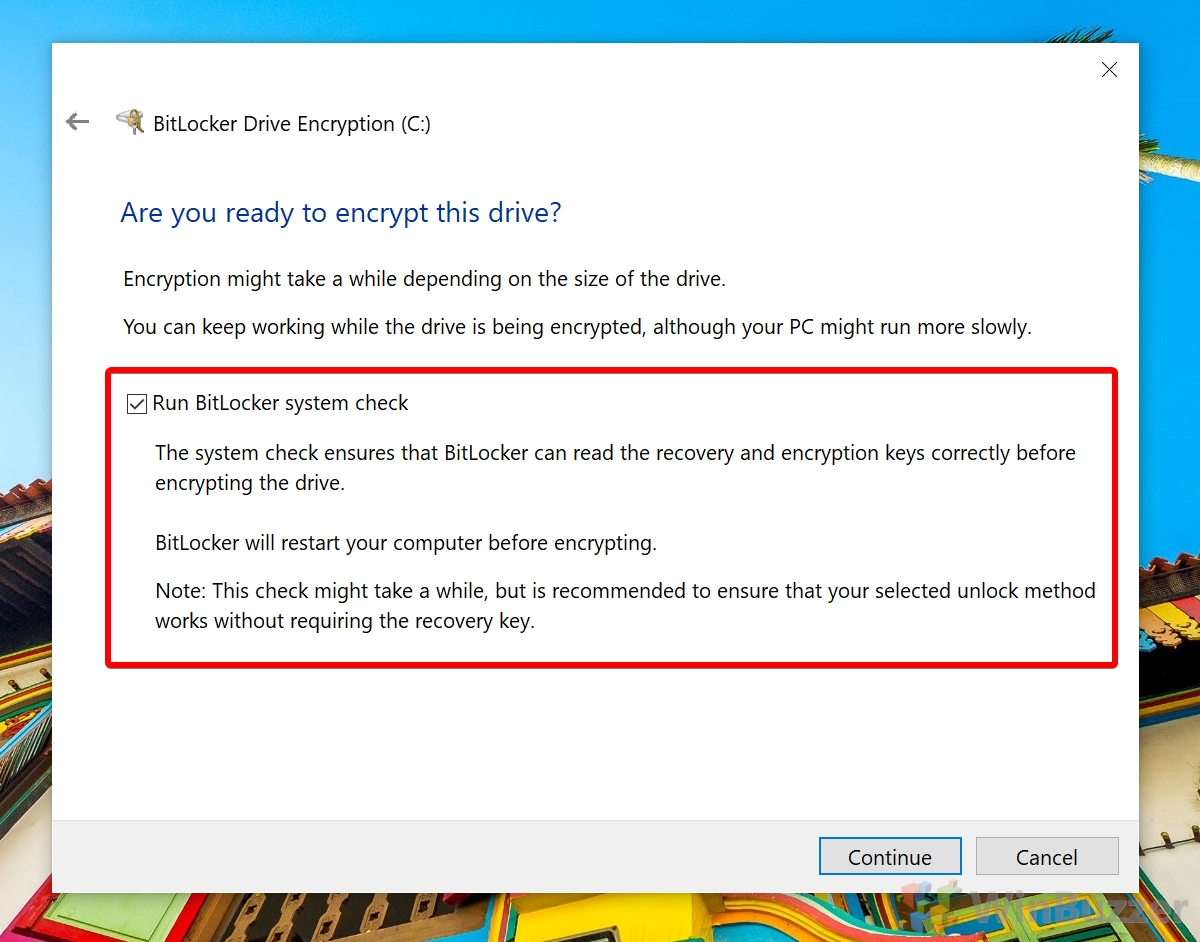
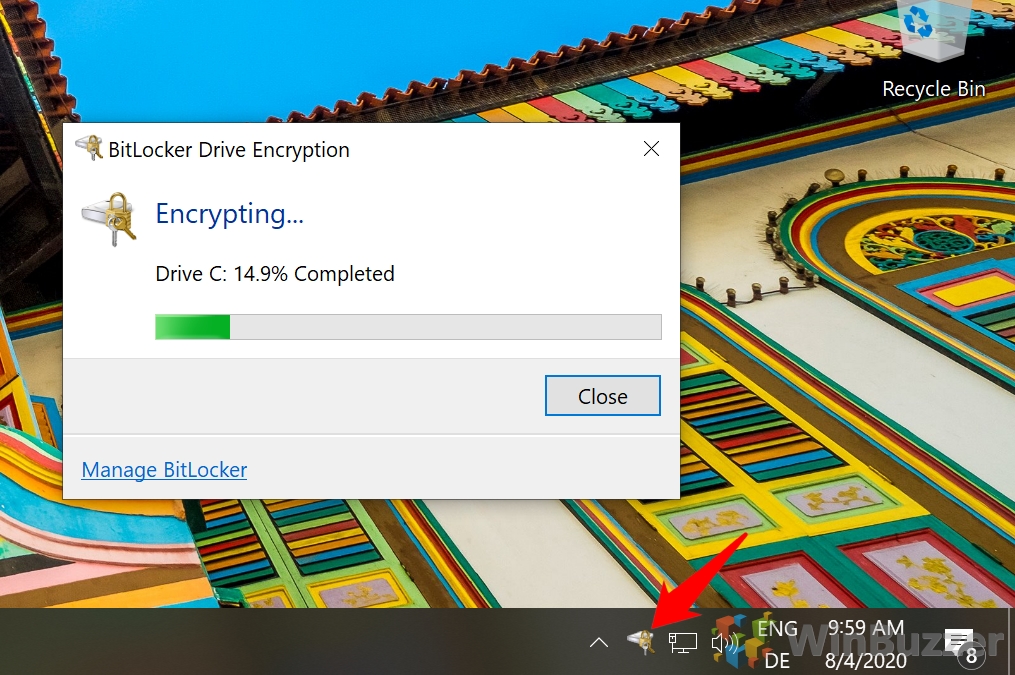
How to Encrypt System Drive with BitLocker
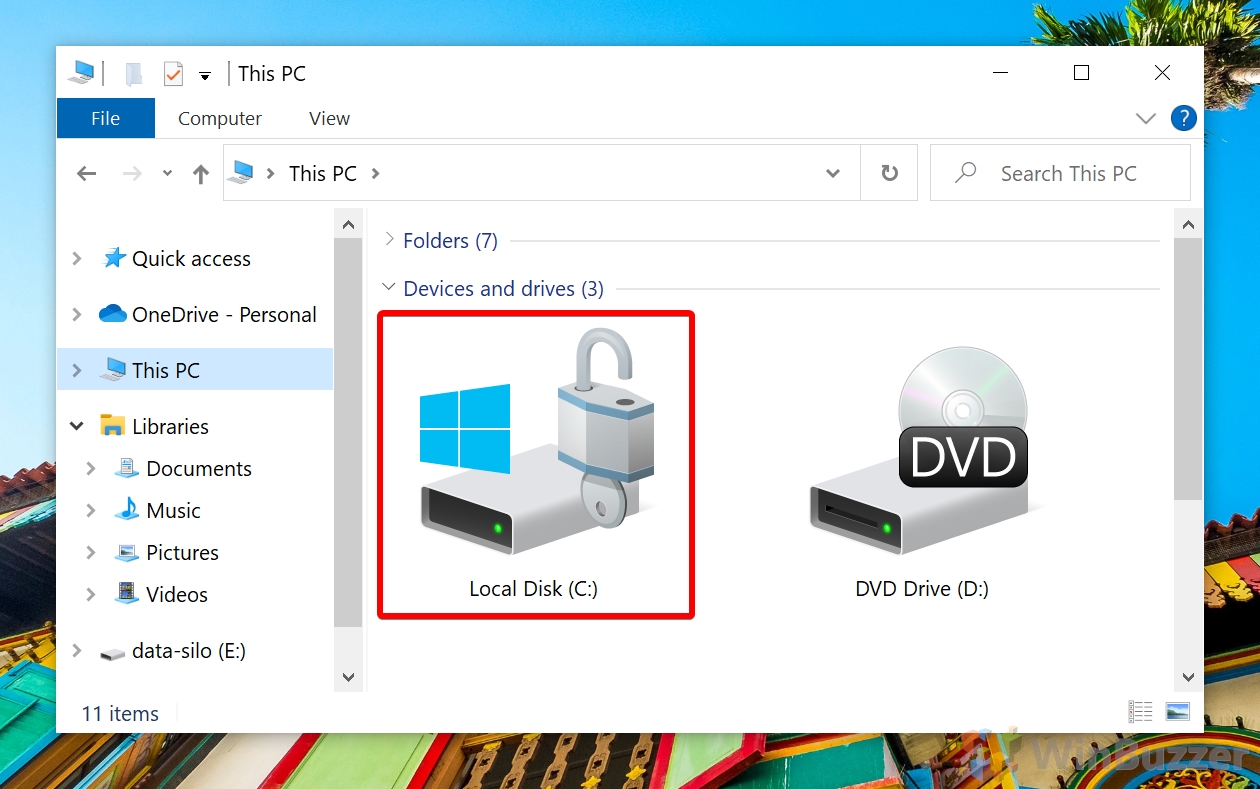
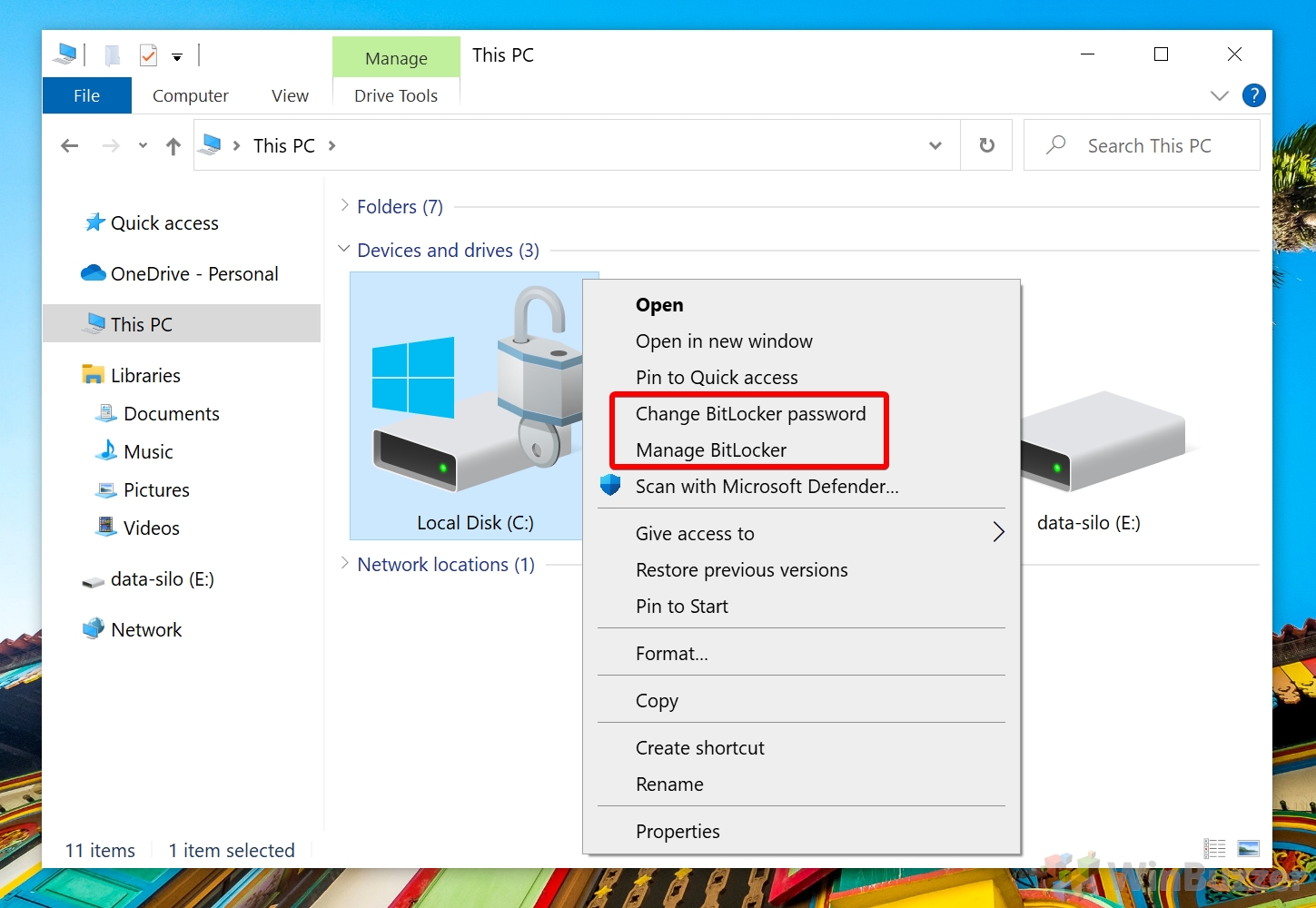
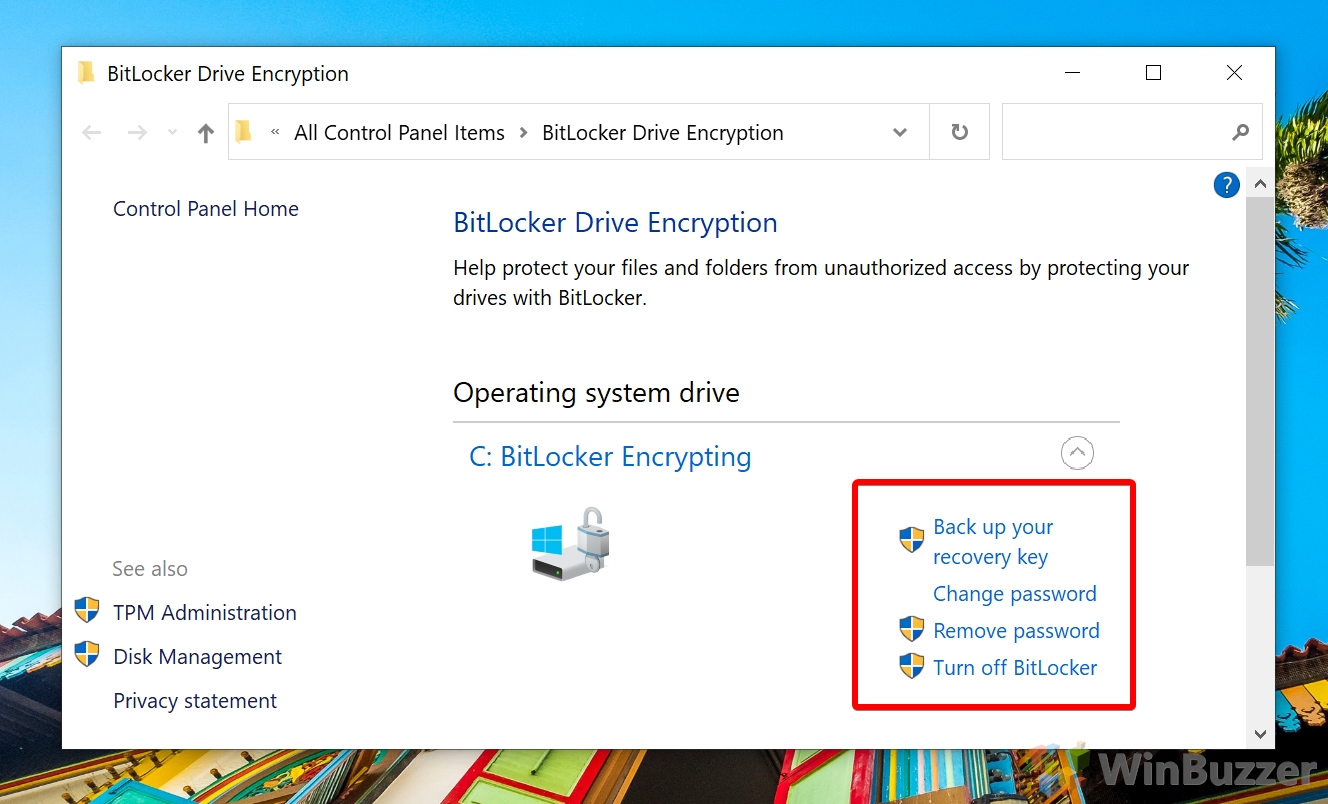
Check Encryption Status and Change Bitlocker Settings for System Drive
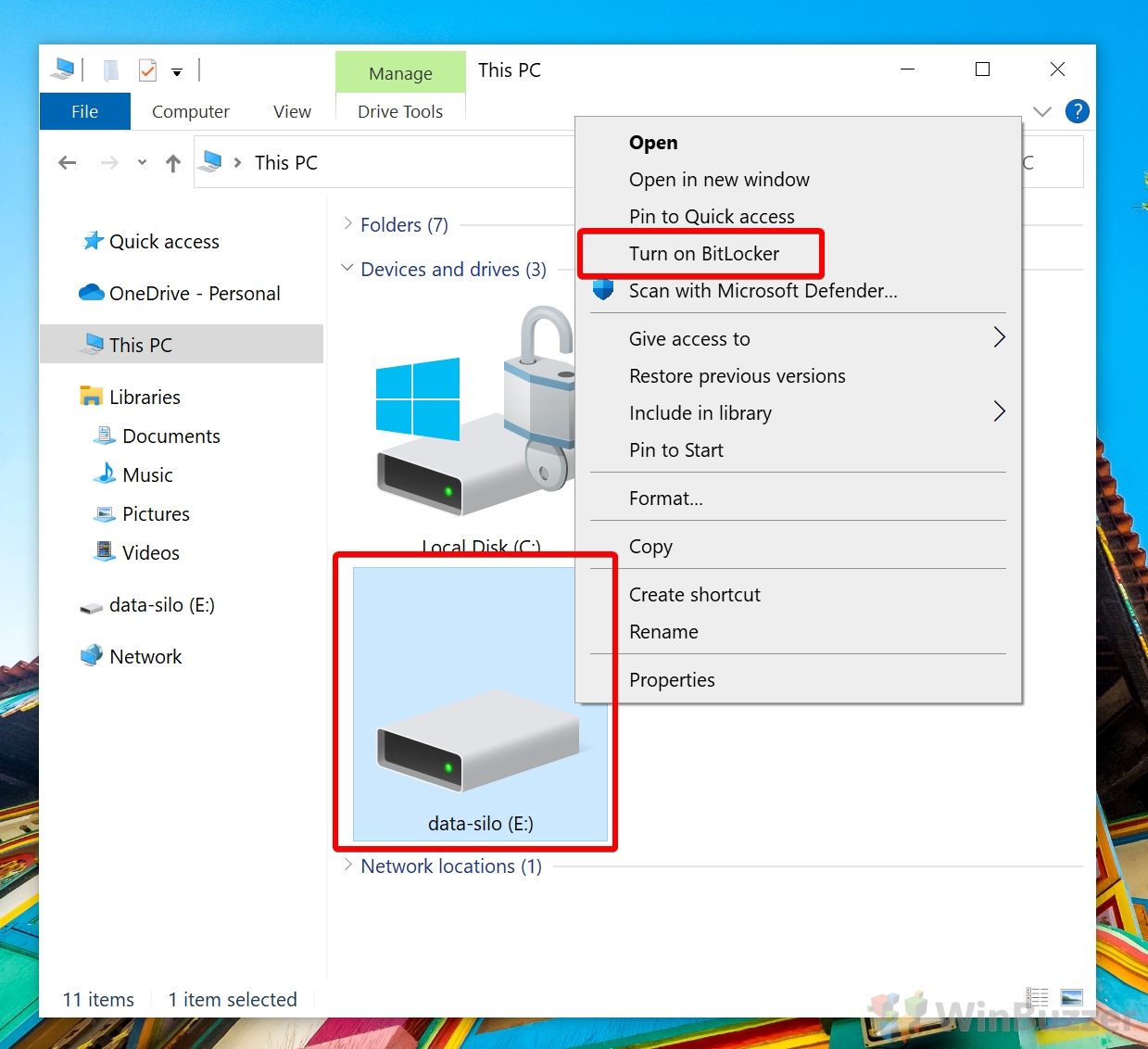
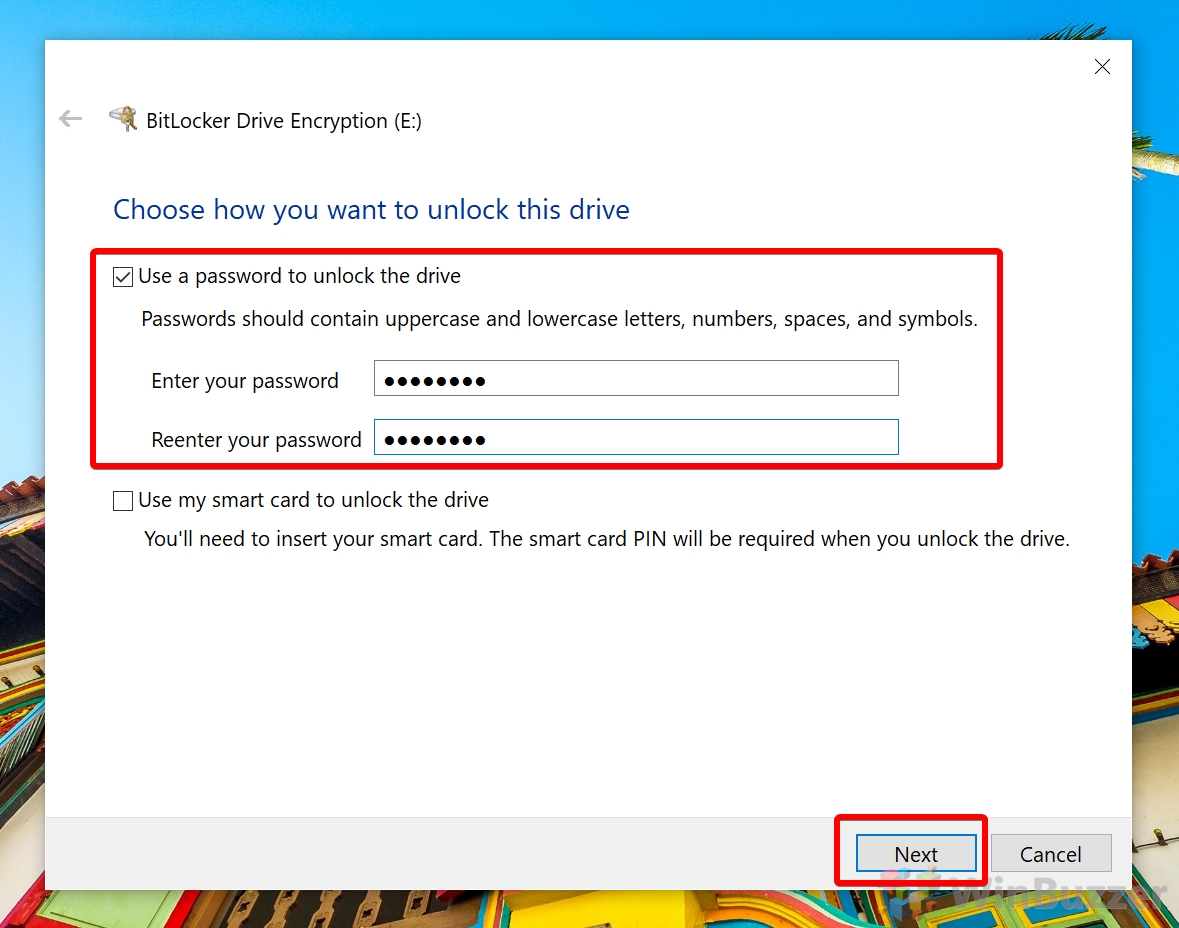
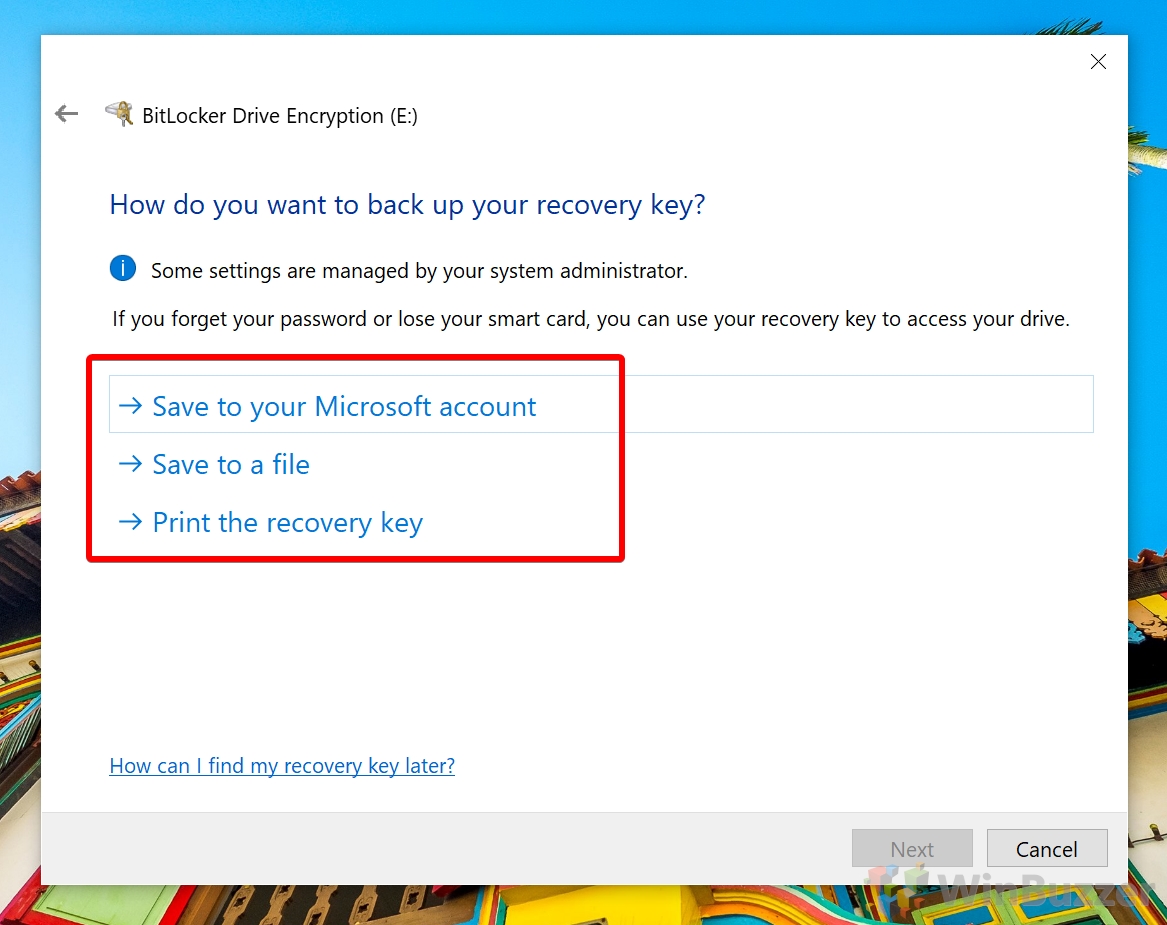
How to Use Bitlocker for non-system disks / BitLocker To Go to Encrypt a USB Drive, External Hard Drive or Secondary Drive
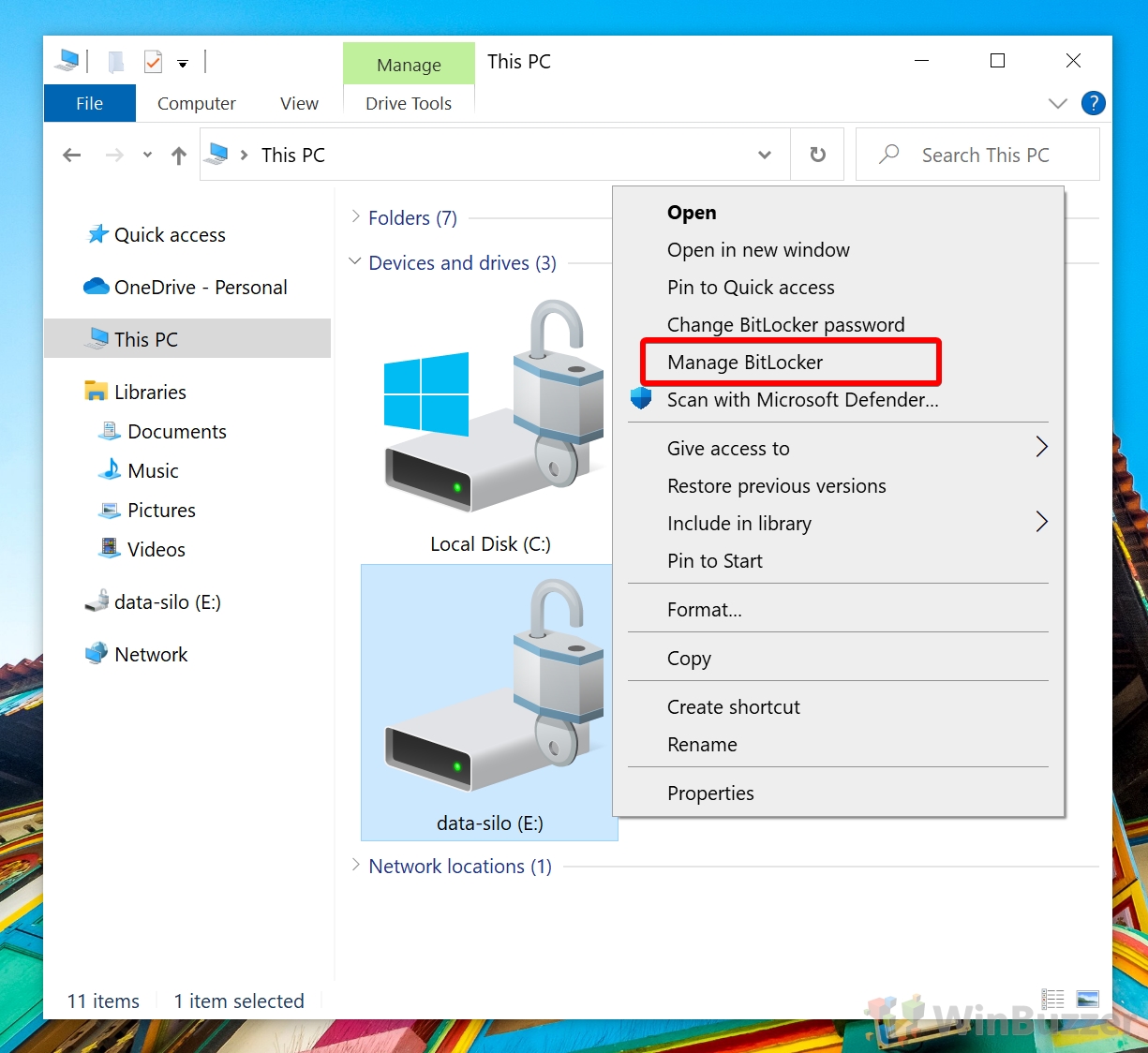
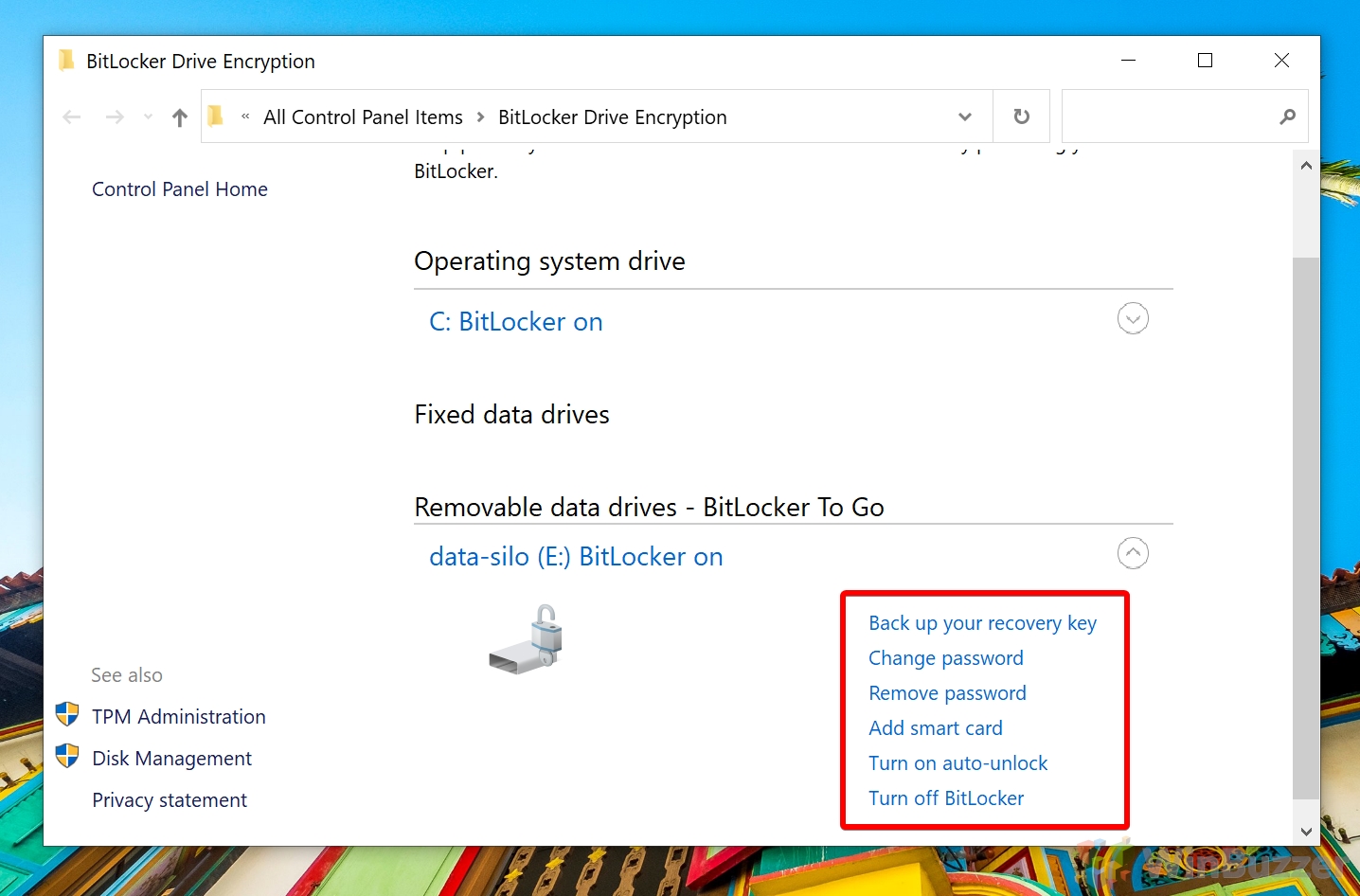
How to Check Encryption Status and Change BitLocker Settings for USB Drives / Secondary disks
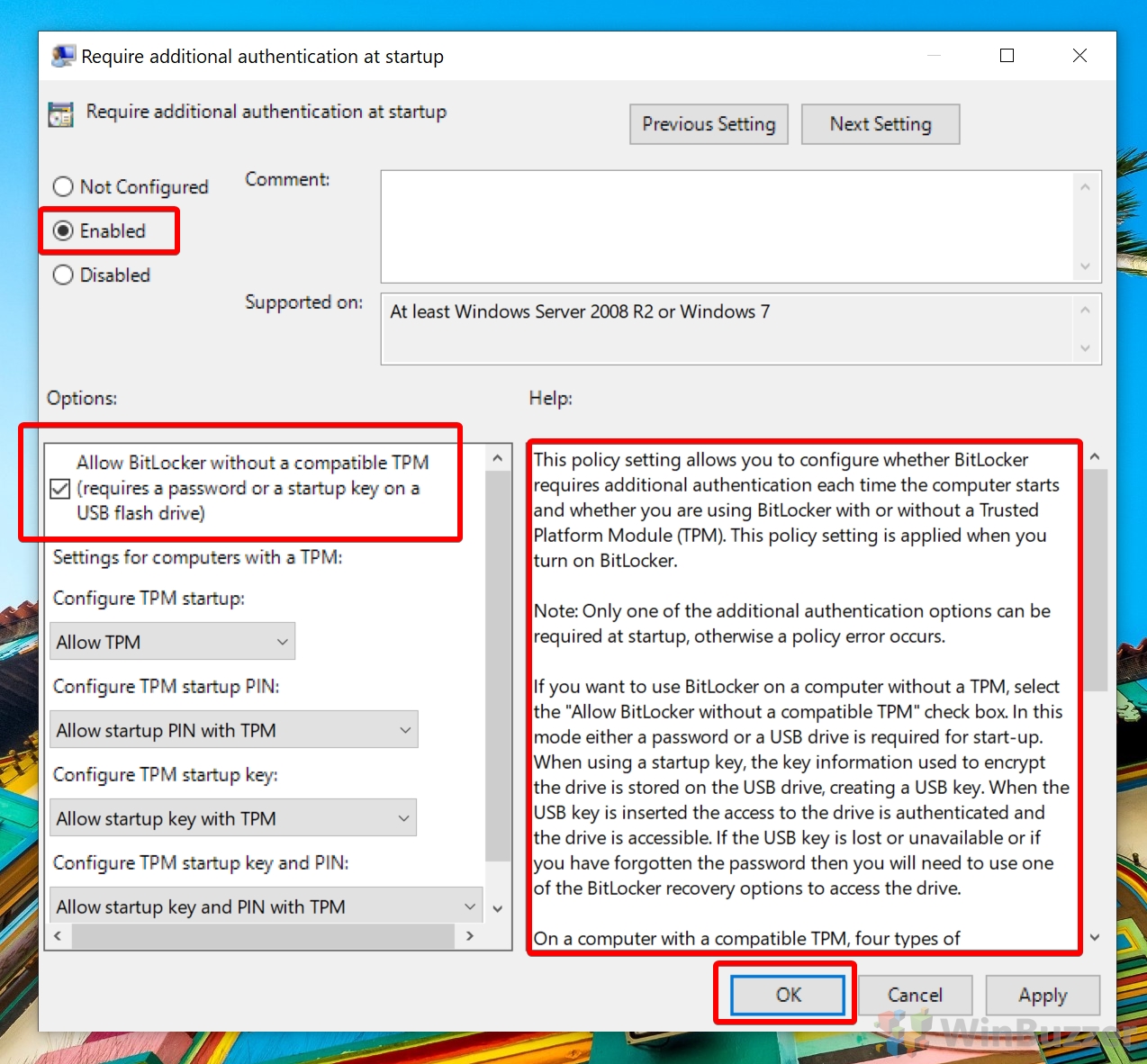
Double-click the “Require additional authentication at startup” policy.