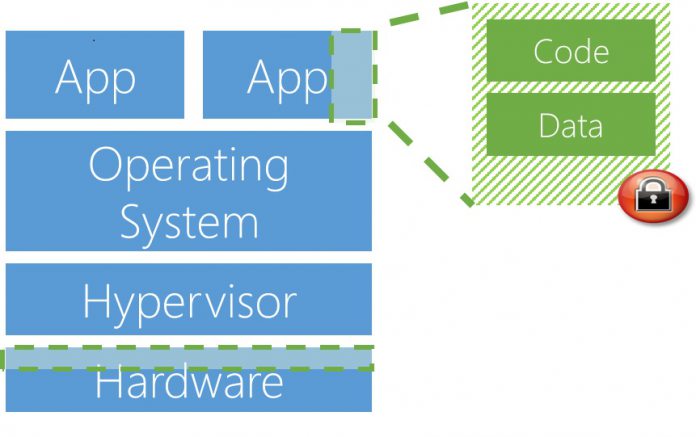
Azure Confidential Computing targets data in use because this is when most attacks happen. According to Azure Chief Technology Officer Mark Russinovich says data breaches are happening daily: “Data breaches are virtually daily news events, with attackers gaining access to personally identifiable information (PII), financial data, and corporate intellectual property. While many breaches are the result of poorly configured access control, most can be traced to data that is accessed while in use…” With the Microsoft and Intel SGX solution deployed, the customer targets the active data by placing it in an enclosed virtual black box. This keeps the data safe, and stops anyone outside from accessing it. The customer is the only party that can access the enclosed data. Obviously, this is to prevent any malicious actors from being able to corrupt the data. Azure Confidential Computing also prevents Microsoft from turning data over to governments when under warrant or subpoenas. The company has often vocally opposed US government acts to take data. Indeed, Microsoft has combatted the U.S. Department of Justice through the courts over various cases of refusing to release customer data. “They can be sure that they can’t do any better than this on their own premises,” Russinovich explains. “This data is completely protected from us and from any attackers.”
Availability
Microsoft has launched Azure Confidential Computing in preview starting today. The service gives cloud customers two ways to secure their data. Microsoft uses its own servers, but alternatively customers can also use in-built security features in Intel’s chops. Data enclaves have been part of Intel’s technology since 2015, but did not plan to integrate it with servers for several years. Microsoft worked with its long-time partner to bring the enclaves to servers more rapidly.