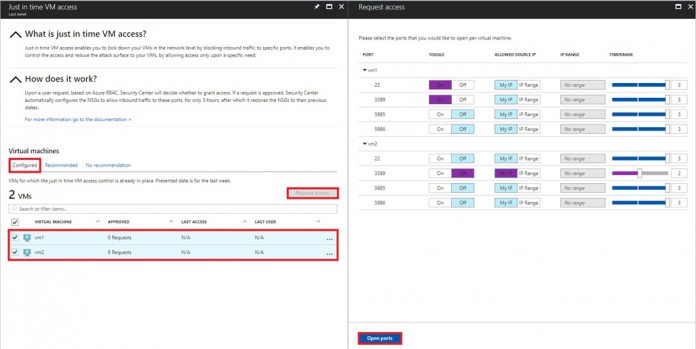
JIT VM Access reduces exposure to brute force and port scanning attacks. It achieves this by giving Azure Security Center customers the ability to deny persistent access when providing controlled access to VMs. “When JIT VM Access is enabled, Azure Security Center locks down inbound traffic to defined ports by creating Network Security Group rule(s),” writes Ben Kliger, Azure senior product manager. “You can request access to the VM when needed, which opens the needed port for an approved amount of time, from approved IP addresses, and only for users with proper permissions. Requests are logged in the Azure Activity Log, so you can easily monitor and audit access. You can also enable JIT VM Access, configure policies and request access through Powershell cmdlets.” Microsoft says that the most common type of cyberattack against cloud services are brute force or port scanning threats. Normally these attacks target ports like RDP and SSH when they are left open during administration access. Users need to be able to grant admin access, but they also want to know their VMs are protected. JIT VM Access alerts users when attacks happen. Additionally, it will also drastically reduce the exposure time to these types of attack.
JIT VM Access in Action
Azure will recommend when the service should be applied to existing VMs and new creations. Once enabled, the feature blocks inbound traffic within set ports. Customers can still access the virtual machine when they need to, but the port will only be open for a defined amount of time. Additionally, the port will only be opened if the IP address is approved. All requests to access the VM are logged in the Azure Activity Log. This allows admins to see who wanted VM access and audit accordingly.